For IT teams, data inconsistencies are top of mind and can often lead to many a sleepless night wondering if the source and target will match when a migration is done. How do you prove the data is consistent bit by bit throughout the migration process and ensure a successful outcome? Continue reading to learn the answer to how DobiMigrate® solves this and other common file and object migration challenges.
When moving data between two disparate systems, it is imperative to validate as much information as possible about the source and target directory structures or else face financial and legal consequences for data irregularities. Compliance laws, such as General Data Protection Regulation (GDPR) in the EU and the California Consumer Privacy Act (CCPA) in the US, have made data integrity a top priority. Unfortunately, without careful consideration, data inconsistencies will occur.
While there are several different reasons why inconsistencies happen, the most common one is that the software moving the data can’t maintain the level of consistency needed. Thankfully, DobiMigrate has the most feature-rich capabilities in the migration space. Below, we detail what sets DobiMigrate apart from other vendors.
Our File Browser and Chain of Custody
Our browsing component and its feature set allow a user to confirm, contrast, and compare the file structures of both source and target devices as shown in Figure 1. As alluded to above, the uncertainty of file consistency from two different systems can keep a person up at night wondering if the data has been copied correctly with all the same permissions and security, bit by bit. With our file browser, you have the ability to confirm and report back the consistency of the data that is copied.
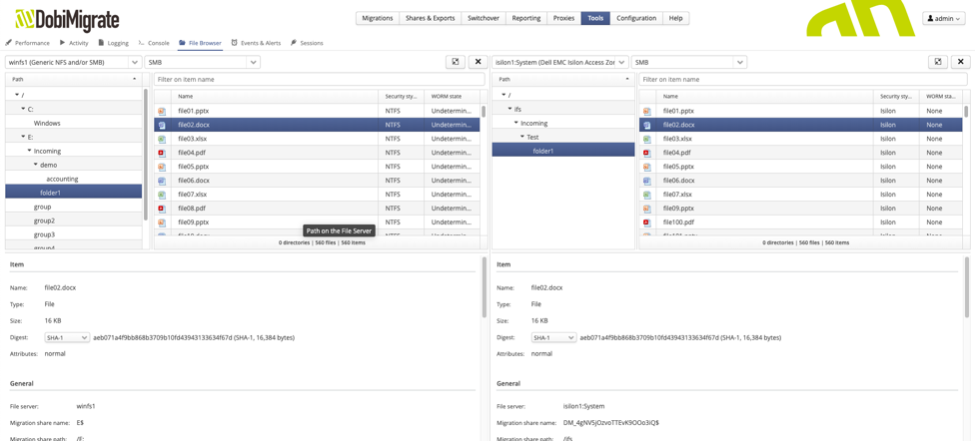
Figure 1
In addition, DobiMigrate provides a chain-of-custody report that complements the file browser comparison with an automatically produced document that confirms the integrity of the data throughout the entire migration. Being able to perform a side-by-side comparison is invaluable to validate and potentially change or confirm the directory structure. Figure 2 shows accessing the chain-of-custody data that is the full count of the directories migrated in addition to the individual files. The chain-of-custody data is downloadable to a compressed “.csv” file, which can then be imported to the database or reporting tool of your choice.
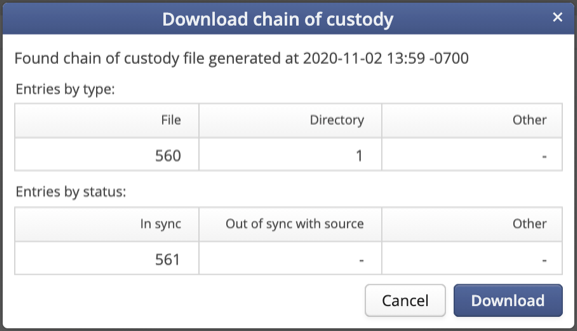
Figure 2
The Hash Digest
Each file in the chain of custody is accounted for along with the hash digest for that file, as seen in Figure 3. The hash digest, typically represented as a character string of x length, is produced from the root of the source data itself and represents that data at a point in time. In DobiMigrate, only a single digest value is shown because this represents the binary “fingerprint” of the file; it’s this same value that is compared between the source and target system to certify that the data was copied accurately and without any corruption.
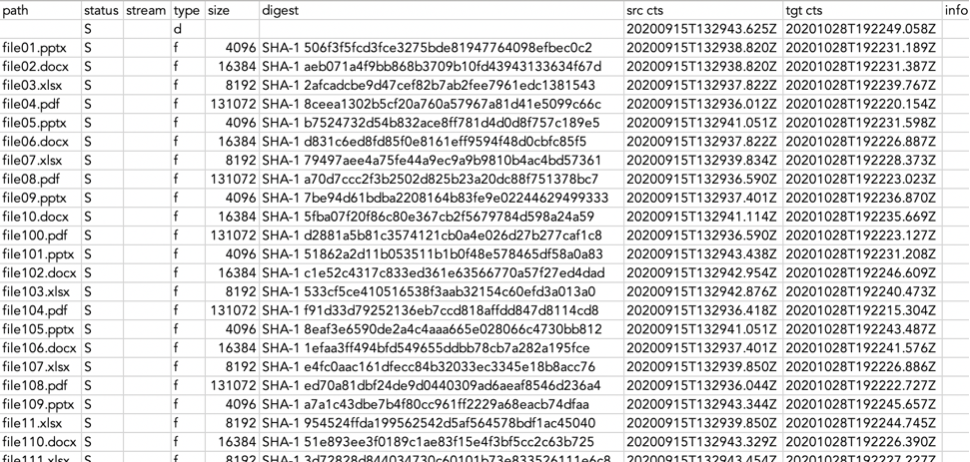
Figure 3
DobiMigrate can use a variety of hashing algorithms that confirm data integrity between a source and target, while many competitors only offer a single hashing option or no option at all. DobiMigrate currently supports five methods of hashing, SHA-1 (selected by default), SHA-256, SHA-512, MD5, and (shortly) XXH128. The difference of each method and why it matters is specific to each organization’s needs, but for the most part a fast and accurate hashing algorithm is often the one that gets used.
Even a single bit change in the source data will completely alter the hash value associated with it. If the hash does not match, Datadobi will invalidate that copy, preventing it from being transferred, and launch an investigation so the situation can be remedied.
A Browsable Experience
When viewing information about your shares and their metadata, Datadobi makes it easier than other methods by giving users a browsable experience, as seen in Figure 4.
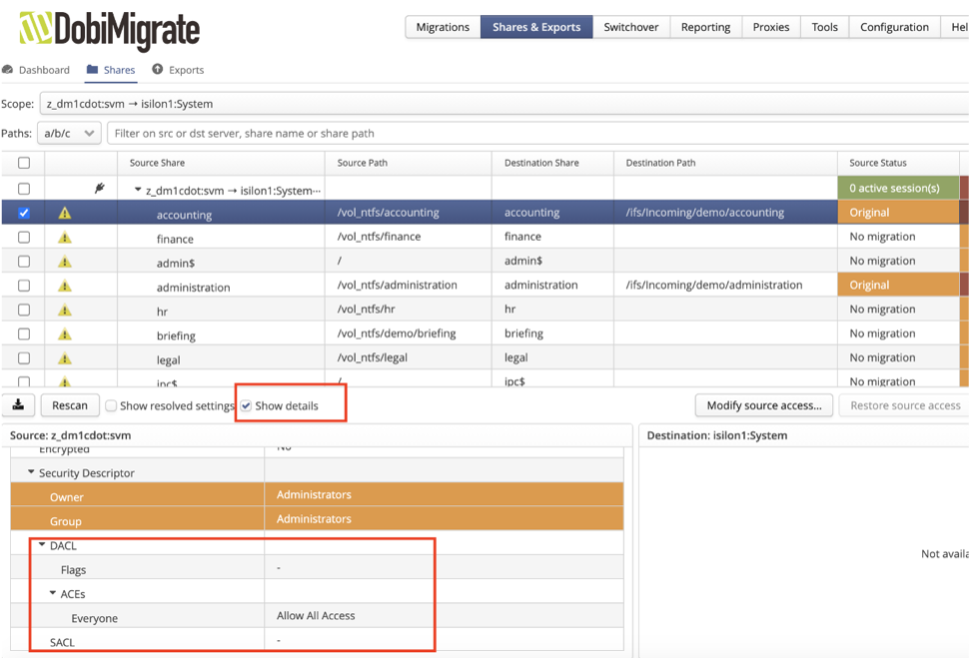
Figure 4
Figure 4 illustrates the share tab option, which calls out important information around the share and its metadata. The directory access control list (DACL), access control entry (ACE), and system access control list (SACL), along with other descriptive information, allow for a quick confirmation of the policies in place. Customers can see the source and destination share naming conventions, along with any compatibility issues that may have been encountered.
Eliminating Roadblocks
During the cutover window, it is not uncommon to have stragglers that don’t read the memo about the downtime event. Typically, you could use the CMC (computer management console) to disconnect users, but that requires connecting to and opening another system or console. DobiMigrate has the ability to kick Windows users out of active sessions during the cutover window from a single pane of glass, as shown below in Figure 5.
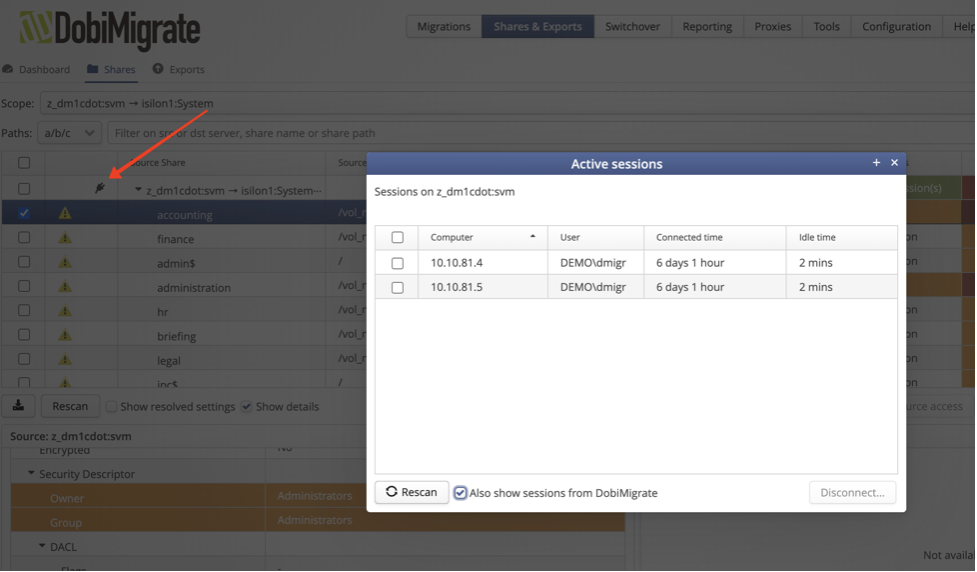
Figure 5
Don’t let data inconsistencies keep you up at night. Use DobiMigrate to help your organization’s data migration go as painlessly as possible.
How to Purchase DobiMigrate
For more information, including how to purchase DobiMigrate, please visit the DobiMigrate product page.

